Entities
View all entitiesCSETv0 Taxonomy Classifications
Taxonomy DetailsProblem Nature
Specification, Robustness
Physical System
Consumer device
Level of Autonomy
Low
Nature of End User
Amateur
Public Sector Deployment
No
Data Inputs
One billion training images, infrared facial scan of individual user
CSETv1 Taxonomy Classifications
Taxonomy DetailsIncident Number
26
Special Interest Intangible Harm
no
Date of Incident Year
2017
Date of Incident Month
11
Date of Incident Day
10
Estimated Date
No
Risk Subdomain
2.2. AI system security vulnerabilities and attacks
Risk Domain
- Privacy & Security
Entity
Human
Timing
Post-deployment
Intent
Intentional
Incident Reports
Reports Timeline

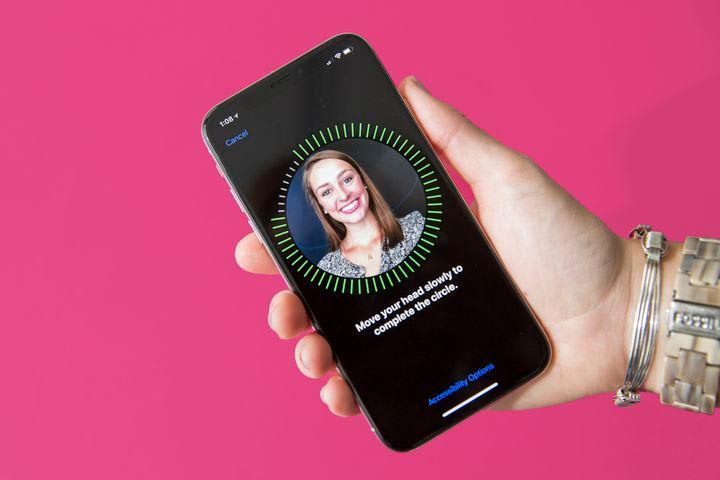
Apple's brand new iPhone X (pronounced 'Ten' by the way) has gone one step further to secure your smartphone by doing away with the Touch ID fingerprint scanner and will now use your face to unlock the device.
Using a new system called Face…

When Apple announced the iPhone X last month—its all-screen, home-button-less, unlock-with-a-look flagship—it placed an enormous bet on facial recognition as the future of authentication. For hackers around the world, Face ID practically pa…

ES Lifestyle newsletter The latest lifestyle, fashion and travel trends ES Lifestyle newsletter The latest lifestyle, fashion and travel trends Enter your email address Continue Please enter an email address Email address is invalid Fill ou…

A Vietnamese company was recently able to trick Apple's facial recognition security feature, but security experts don't believe there's a big risk for business users.
Video: 5 things to know about Apple's Face ID Curious about Apple's Face …

Apple's new Face ID unlock system on the iPhone X can reportedly be tricked with paper eyes and pizza toppings.
Yes, you read that correctly, but let us explain. Life-size eyes printed onto paper, then placed on the face of a 'sleeping' iPh…
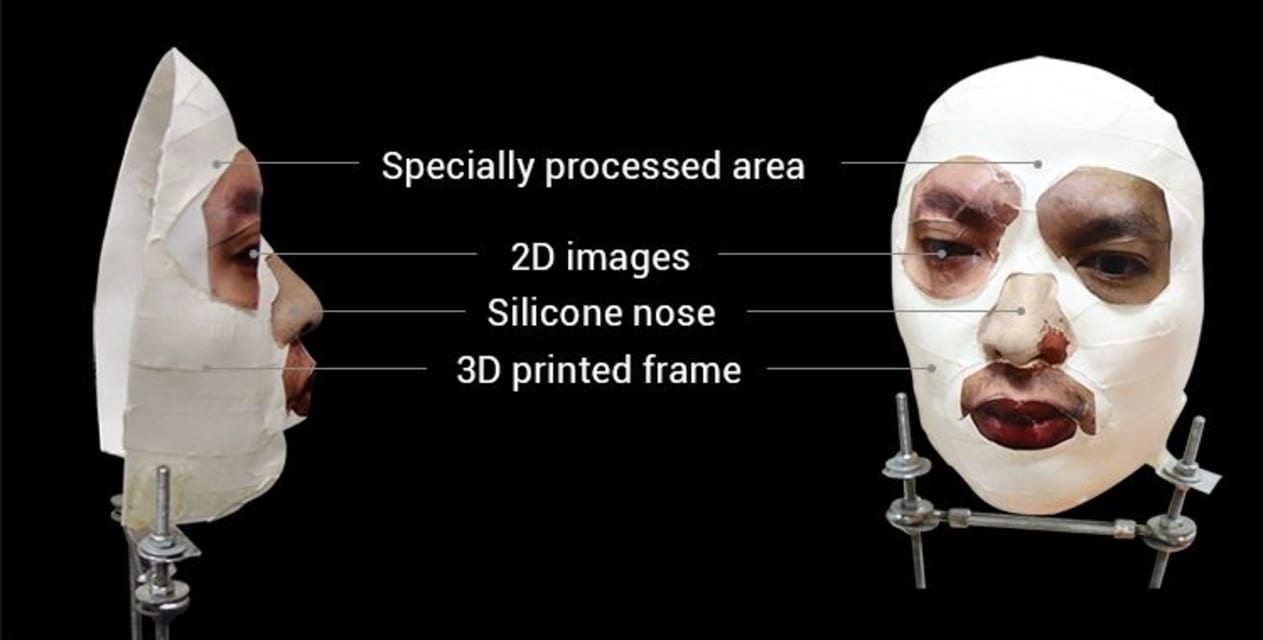
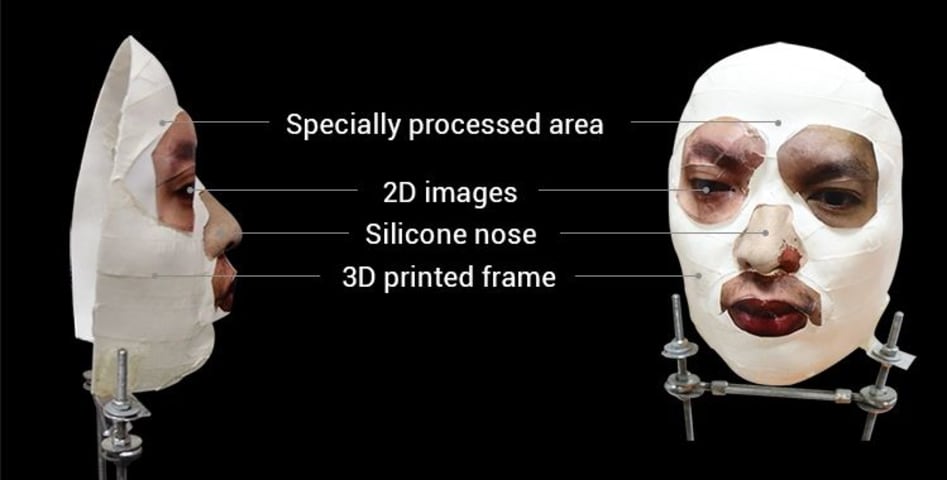
Apple claims the facial recognition system on the new iPhone X is impervious to being fooled by photos, impersonators and masks, but a team of hackers claim to have beaten the technology after just a week.
Cyber security firm Bkav says a 3D…

Hackers may have already proven that Face ID isn’t quite as secure as secure as Apple claims.
Using a simple 3D printed mask, Vietnamese security firm Bkav, has posted a video showing an iPhone X being unlocked after unveiling a composite 3…

This article has been updated below with another, more convincing video demonstration of Bkav's Face ID spoofing, which the firm revealed two weeks after the original.
When Apple released the iPhone X on November 3, it touched off an immedi…

BKAV
Did Apple's vaunted Face ID facial recognition system on the iPhone X already get hoodwinked?
That's what a Vietnamese security company says it did -- using only a $150 3D-printed mask. BKAV uploaded a video demonstration as a proof of…

Apple no longer wants you to unlock your iPhone with touch. With the iPhone X, it’s all about your face.
Face ID was the standout feature of the iPhone X, and one that differentiates it from the iPhone 8 range and anything that’s come befor…
Security researchers say they used a $150 mask to break the Face ID facial recognition system that locks Apple's new iPhone X. The work may be a significant, it may be little more than a stunt with few real-world consequences, or it could p…

It's one of the most wanted features in the iPhone X, but it seems that Face ID may not be as safe as Apple thinks.
Cyber-security researchers claim they have fooled the face recognition technology with a mask that costs just £114 ($150) to…

When Apple first announced Face ID for the iPhone X, it claimed the new feature was significantly more secure than Touch ID and couldn’t be fooled by even the most realistic of masks. But it turns out that might not be the case.
Vietnamese …
Https%3a%2f%2fblueprint api production.s3.amazonaws.com%2fuploads%2fvideo uploaders%2fdistribution thumb%2fimage%2f82967%2f7e1f7535 a028 4885 9984 973f49d6cd0c More
There is no such thing as foolproof phone security.
Case in point: Security…

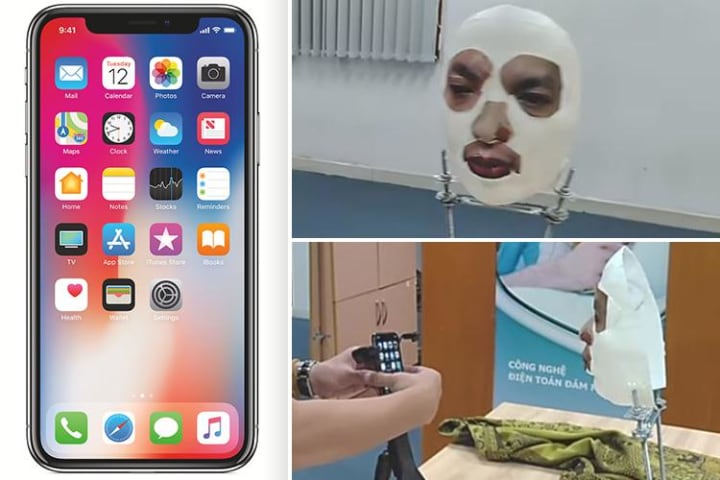
A researcher in Vietnam has demonstrated how he apparently fooled Apple‘s face recognition ID software on its new iPhone X using a mask made with a 3D printer, silicone, and paper tape.
An announcement on Friday by Bkav, a Vietnamese cybers…
IT'S barely been available for ten days, but conniving hackers have already cracked the iPhone X's facial recognition security system.
Security experts based in Singapore used a 3D scanner to re-create the owners face at a cost of £115.
You…

IT TURNS out Apple’s Face ID is far from perfect, as demonstrated by a 10-year-old boy who is the latest to “hack” the sophisticated technology.
How did he do it?
By simply looking like his mum.
Ammar Malik was able to break into his mum’s …

Face ID, Apple's facial identity sensor for iPhone X, is new and that's both scary and ripe for exploitation. We saw it happen with Touch ID, from all the concern that manifested when Apple announced it alongside iPhone 5s to the sensationa…

It only took a week:
On Friday, Vietnamese security firm Bkav released a blog post and video showing that -- by all appearances -- they'd cracked FaceID with a composite mask of 3-D-printed plastic, silicone, makeup, and simple paper cutout…

A researcher in Vietnam has demonstrated how he apparently fooled Apple's face recognition ID software on its new iPhone X using a mask made with a 3D printer, silicone and paper tape.
An announcement on Friday by Bkav, a Vietnamese cyberse…

The Vietnamese hackers who claimed earlier this month to have fooled Apple's Face ID with a mask costing less than $150 are back. But this time, their evidence is more compelling.
Whereas in their previous attack researchers from Vietnamese…

iPhone X’s Face ID keeps getting tricked.
As pointed out by Forbes, researchers at the Vietnamese security firm Bkav have found another way to bypass Apple’s facial recognition system. The team, which pulled off a similar hack earlier this …

Vietnamese hackers who previously said they could bypass Apple’s Face ID biometric phone security with a mask claim to have hacked the iPhone X again, this time with more evidence of their success.
According to news from Forbes, Vietnamese …
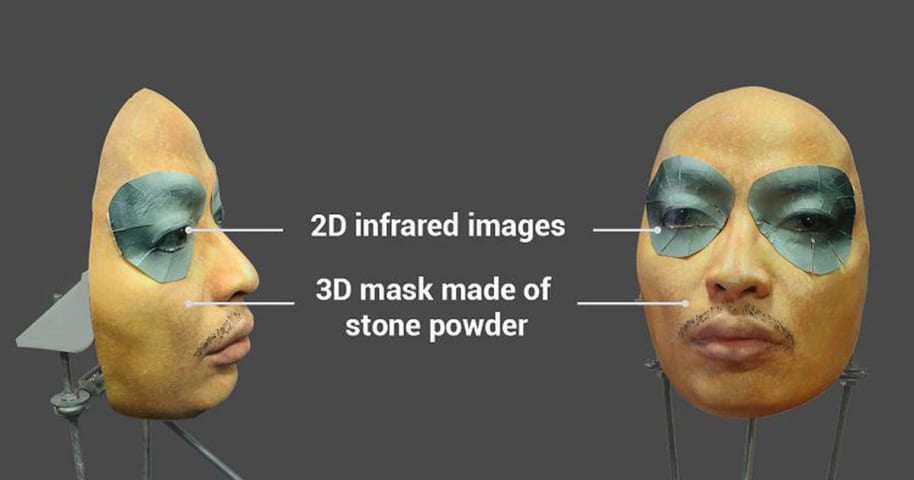
Breaking into a locked iPhone X shouldn't ever be described as simple, but according to a group of security researchers, that's exactly where we find ourselves.
The same Vietnamese team that managed to trick Face ID with an elaborately cons…
Variants
Similar Incidents
Did our AI mess up? Flag the unrelated incidents

Deepfake Obama Introduction of Deepfakes

FaceApp Racial Filters
Similar Incidents
Did our AI mess up? Flag the unrelated incidents

Deepfake Obama Introduction of Deepfakes